Fake Exhibitions Mac OS
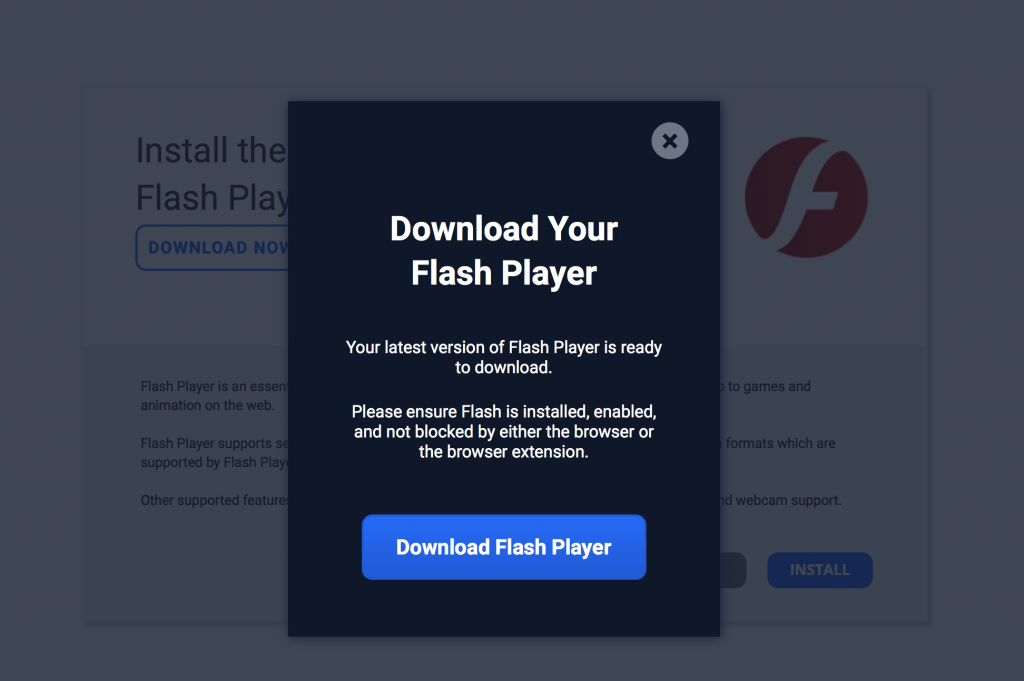
A phishing scam has targeted Mac users by redirecting them from legitimate websites to fake websites which tell them that their computer is infected with a virus. The user is then offered Mac Defender 'anti-virus' software to solve the issue.
This “anti-virus” software is malware (i.e. malicious software). Its ultimate goal is to get the user's credit card information which may be used for fraudulent purposes.
The most common names for this malware are MacDefender, MacProtector and MacSecurity.
Apple released a free software update (Security Update 2011-003) that will automatically find and remove Mac Defender malware and its known variants.
The Resolution section below also provides step-by-step instructions on how to avoid or manually remove this malware.
Resolution
How to avoid installing this malware
- PRANK: macOS Updates.
- Fake is a new browser for Mac OS X that makes web automation simple. Fake allows you to drag discrete browser Actions into a graphical Workflow that can be run again and again without human.
- Virus Alert from Apple pop-up is a social engineering attack that tries to con you and other unsuspecting users into calling a fake Apple Support. Security professionals have determined that users are rerouted to the “Virus Alert from Apple” scam by adware or from malicious advertisements. Adware can cause problems for your machine.
If any notifications about viruses or security software appear, quit Safari or any other browser that you are using. If a normal attempt at quitting the browser doesn’t work, then Force Quit the browser.
In some cases, your browser may automatically download and launch the installer for this malicious software. If this happens, cancel the installation process; do not enter your administrator password. Delete the installer immediately using the steps below.

- Go into the Downloads folder, or your preferred download location.
- Drag the installer to the Trash.
- Empty the Trash.
How to remove this malware
MacOs-Linux, an operating system based on Ubuntu 11.04 (Natty Narwhal) that imitates Mac OS X as closely as possible, is now available for download. After the downfall of Pear OS, which was the.
If the malware has been installed, we recommend the following actions:
- Do not provide your credit card information under any circumstances.
- Use the Removal Steps below.
Removal steps
- Move or close the Scan Window.
- Go to the Utilities folder in the Applications folder and launch Activity Monitor.
- Choose All Processes from the pop up menu in the upper right corner of the window.
- Under the Process Name column, look for the name of the app and click to select it; common app names include: MacDefender, MacSecurity or MacProtector.
- Click the Quit Process button in the upper left corner of the window and select Quit.
- Quit Activity Monitor application.
- Open the Applications folder.
- Locate the app ex. MacDefender, MacSecurity, MacProtector or other name.
- Drag to Trash, and empty Trash.
Malware also installs a login item in your account in System Preferences. Removal of the login item is not necessary, but you can remove it by following the steps below.
- Open System Preferences, select Accounts, then Login Items
- Select the name of the app you removed in the steps above ex. MacDefender, MacSecurity, MacProtector
- Click the minus button
Use the steps in the “How to avoid installing this malware” section above to remove the installer from the download location.
Note: Apple provides security updates for the Mac exclusively through Software Update and the Apple Support Downloads site. User should exercise caution any time they are asked to enter sensitive personal information online.
A new malicious package has been spotted this week on the npm registry, which targets NodeJS developers using Linux and Apple macOS operating systems.
The malicious package is called 'web-browserify,' and imitates the popular Browserify npm component downloaded over 160 million times over its lifetime.
web-browserify is itself built by combining hundreds of legitimate open-source components, and performs extensive reconnaissance activities on an infected system.
Moreover, as of today, the ELF malware contained with the component has a zero detection rate by all leading antivirus engines.
Spawns a persistent, ELF executable on install
This week, a malicious component 'web-browserify' was found on the npm registry.
The component was detected by Sonatype's automated malware detection system, Release Integrity, and deemed malicious after analysis by the Sonatype security research team, that I'm a part of.
'web-browserify' is named after the legitimate Browserify component that scores over 1.3 million weekly downloads and used over by 356,000 GitHub repositories.
The malicious component, 'web-browserify' in contrast is just shy of 50 downloads—before it was pulled from npm within two days of its publishing.
'web-browserify' is created by a pseudonymous author describing themselves to be Steve Jobs.
The package consists of a manifest file, package.json, a postinstall.js script, and an ELF executable called 'run' present in a compressed archive, run.tar.xz within the npm component.
As soon as 'web-browserify' is installed by a developer, the scripts extract and launch the 'run' Linux binary from the archive, which requests elevated or root permissions from the user.
The extracted run binary is approximately 120 MB in size and has hundreds of legitimate open-source npm components bundled within it, that are being abused for malicious activities.
For example, one such component is the cross-platform 'sudo-prompt' module that is used by run to prompt the user for granting the malware root privileges on both macOS and Linux distributions.
Because elevated privileges would be requested almost at the same time 'web-browserify' was being installed, the developer may be misled into believing that it is the legitimate installer activities requiring elevated permissions.
As seen by BleepingComputer, once the ELF acquires elevated permissions, it gains persistence on the Linux system and copies itself to /etc/rot1 from where it subsequently runs on every boot:
Phones home with your info to an 'example' domain
The malware has advanced reconnaissance and fingerprinting capabilities.
It uses another legitimate npm component, systeminformation, to collect the following bits of information from the infected system:
- System username
- operating system information, such as manufacturer/brand
- Information on Docker images
- Bluetooth-connected devices
- Virtual Machines present on the system or if virtualization is enabled
- CPU speed, model, and cores
- RAM size, hard drive capacity, disk layout, system architecture
- Hardware information regarding network cards/interfaces, battery, WiFi, USB devices, etc.
As confirmed by BleepingComputer at least some of this fingerprinting information is exfiltrated to an attacker-controlled domain over a plaintext (HTTP) connection, as GET parameters:
Fake Exhibitions Mac Os Download
Of particular note is the domain used by the attacker for carrying out these activities:
Although at the time of our analysis, BleepingComputer observed the server where the domain points to is responding with a 404 (not found), the word ejemplo means 'example' in Spanish.
A domain such as ejemplo.me can therefore easily be mistakenly conflated with legitimate test domains, such as example.com cited by applications and their documentation.
Additionally, under certain circumstances, the malware attempts to remove the contents of the /etc/ directory and disable critical Unix services by tampering with the systemctlutilityand the systemd directory.
Zero VirusTotal detection rate
Despite the malware engaging in outright nefarious activities by abusing legitimate open-source components, it has a perfect zero score on VirusTotal, at the time of our analysis.
Fake Exhibitions Mac Os 11
The fact that it uses genuine software applications to perform shady activities could be one of the reasons that no antivirus engine has been able to flag this sample yet (the sample itself was submitted to VirusTotal on April 10th, 2021).
Fake Exhibitions Mac Os Catalina
It also remains a mystery as to why, the 'web-browserify' component, although caught by Sonatype, was unpublished by its author almost two days later after its initial publishing.
The discovery of yet another npm malware comes after dependency confusion malware was seen targeting known tech companies.
The full extent of capabilities contained within this malware and its definite purpose are yet to be determined.
But, the malware's zero-detection rate and the fact it capitalizes on legitimate open-source components, including the popular Browserify, should raise everyone's eyebrows for what the next iteration of such an attack might look like.